Guidelines for Vehicle Robbery Prevention using Remote Blocking Signals
Keywords:
Vehicle robbery prevention, Remote sensing, Remote control, Radio signal transmissionAbstract
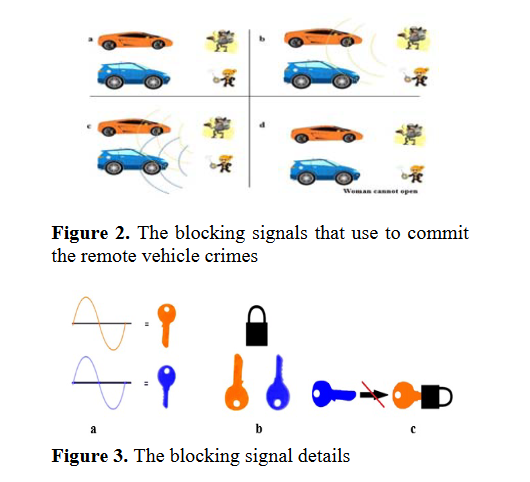
In this paper, the radio signal remote sensing device was used to control the vehicle door switching control, which was the field trials experiment. The switching "On" and "Off" of the switching signals were used to control the vehicle door and investigated. In application, the blocking signal from the commit the remote vehicle crime in the venerable place can be protected. The results obtained have shown that the signal blocking by using another remote control over 5 meters, 10 meters and 15 meters could be achieved. The proposed models and tested results have shown that the Vehicle Brand A Model No. 1 could be blocked by 83.33 percent,
while Brand A Model No.2 by 83.33 percent, Brand B Model No.1 by 40 percent, Brand B Model No.2 by 60 percent, Brand C Model No. 1 by 83.33 percent, Brand C Model No. 2 by 83.33 percent, meanwhile, the remote control for general vehicle are used radio waves with frequency 315 and 433 MHz, where the criminal will use the interference signals to form the blocking (jamming) signals, the vehicle can be robbed.
References
Alchekh Yasin, S.Y., Yrfanean, A.R., Mosavi, M.R., & Mohammadi, A. (2014). An effective approach for simulating the two-color infraredseekers, Infrared Physics & Technology, 67,73–83, doi: 10.1016/j.infrared.2014.05. 004
Ishibashi, Y., & Fukui, M. (2012) Mechanism of the jamming transition in the two-dimensional traffic networks, Physica A: Statistical Mechani-cs and its Applications, 391, 6060-6065, doi: 10.1016/j.physa.2012.06.049.
Olmos, P. M., & Murillo-Fuentes, J. J. (2012). Remote detection of a frequency jammer operating in the down link of a cellular system,Wireless Personnel Communication, 63, 861–870, doi:10.1007/s11277-010-0171-9.
Satyanarayana, K., Sarma, A. D., Sravan, J., Malini, M., & Venkateswarlu, G. (2013). GPS and GPRS based telemonitoring system foremergency patient transportation, Journal of medical Engineering, 13,1-9, doi:10.1155/2013/363508
Wilson, D. (2005). Behind the cameras: monitoring and open-street CCTV surveillance in Australia, Security Journal, 18, 43-54,doi:10.1057/palgra-ve.sj.8340190.
Xiaoqi, L., Baohua, Z., Ying, Z., He, L., & Haiquan, P. (2014).The infrared and visible image fusion algorithm based on target separation and sparse representation, InfraredPhysics & Technology, 67,397-407, doi:10.1016/j.infrared.2014.09.007.
Zhou, L., & Haas, Z. J. (1999). Securing Ad Hoc Networks, IEEE Networks, 13,24-30,doi:10.1109/65.806983.