The Utilization of ISO/IEC 27001:2013 as a Framework for Security Improvement in Accordance with GDPR for SMEs
Keywords:
ISO/IEC 27001:2013, GDPR, Data privacy, SMEs and Personally Identifiable InformationAbstract
General Data Protection Regulation (GDPR) – a regulation from European Union (EU) aims for the security of ‘Personally Identifiable Information’ (PII) of EU residents. It gives an individual a power to have control over the processing of their personal data by organizations. As it is, the regulation does refer to the information security controls needed to ensure the security of PII. In this paper, we propose an information security assessment on management of PII for Small and Medium-sized Enterprises (SMEs)by incorporating ‘ISO/IEC 27001:2013 Annex A. Reference control objective and controls.’into the management of PII in accordance with GDPR for PII security improvement. We have determined that following the quantitative research method is appropriate as this research is aimed to determine the existence of information security controls applicable to the management of PII within the organization. A set of questions was created for interview with sampled organizations to determine the existence of information security controls according to ‘ ISO/ IEC 27001: 2013 Annex A. Reference control objective and controls.’.Content analysis where pre-existing records and evidence will be requested and reviewed will also be applied to ensure that the information security controls is actually implemented.
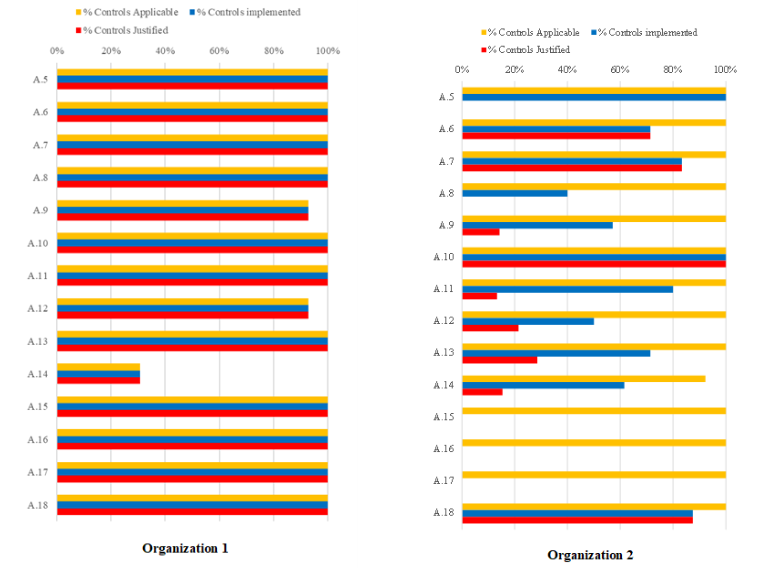
It was found that in most organizations, however, there exists a good coverage of the information security controls according to ‘ISO/IEC 27001:2013 Annex A. Reference control objective and controls.’, buthave difficulty providing evidence justifying the adequacy of the information security control implemented. This is mainly due to the lack of management systems to justify the adequacy of various security controls implemented in the first place.
‘ISO/IEC 27001:2013’ may be used as a framework for PII security control assessment to justify the adequacy or improve upon various security controls implemented for PII
References
Clements, T., & Milton, S. (2018). Maintaining data protection and privacy beyond GDPR implementation. ISACA.
Díaz, E. D. (2016). The new European Union General Regulation on Data Protection and the legal consequences for institutions. Church, Communication and Culture, 1(1), 206-239.
Irwin, L. (2018, August 31). How ISO 27001 can help you achieve GDPR compliance. Retrieved from it governance: https://www.itgovernance.co.uk/blog/howiso-27001-can-help-you-achieve-gdprcompliance
ISO Copyright Office. (2013). ISO/IEC 27001 Information technology—Security techniques—Information security management systems—Requirements. INTERNATIONAL. ISO Copyright Office.
ISO27k Forum. (2016). ISO 27001 Security. Mapping between GDPR (the EU General Data Protection Regulation) and ISO27k, 1-19.
Lopes, I., Guarda, T., & Oliveita, P. (2019). How ISO 27001 can help achieve GDPR compliance. 14th Iberian Conference on Information Systems and Technologies (CISTI), 1-6.
Middleton-Leal, M. (2018). GDPR and ISO 27001 Mapping: Is ISO 27001 Enough for GDPR Compliance? Retrieved from netwrix: https://blog.netwrix.com/2018/04/26/gdprand-iso-27001-mapping-is-iso-27001-enough-for-gdpr-compliance/
Punit, B. (2018). Intro to GDPR-A Plain English Guide to Compliance. Croatia, EU: Advisera Expert Solutions Ltd.
Thai Winner. (2020, August 11). Retrieved from https://thaiwinner.com/what-is-sme/
The European Parliament and the Council of the European Union. (2016). Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016. Official Journal of the European Union.
Tzolov, T. (2018). One model for implementation GDPR based on ISO standards. International Conference on Information Technologies (InfoTech-2018), 1-3.